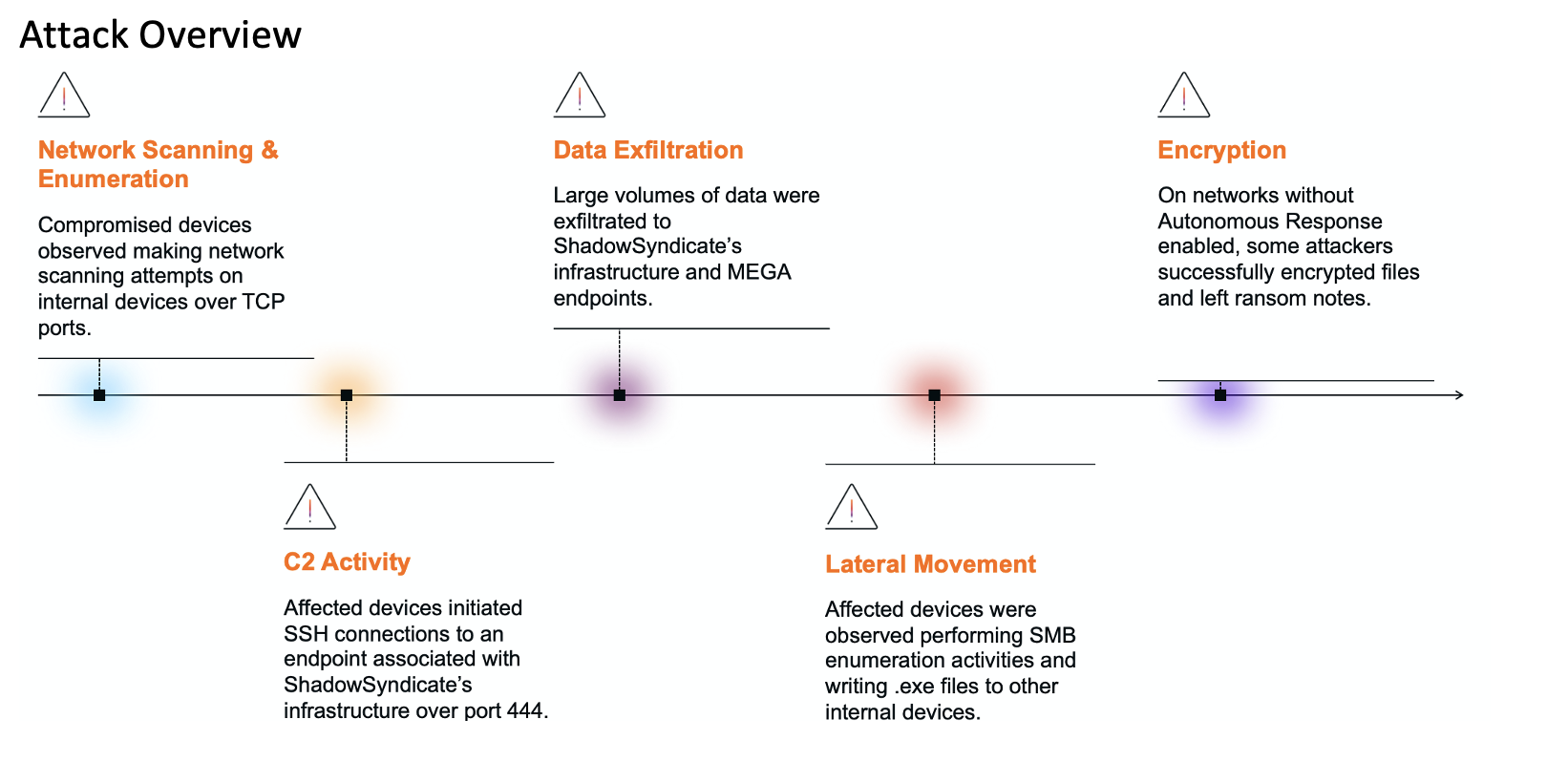
Darktrace security members and researchers have recently seen a rise in what we are calling Safelink Smuggling. Safelinks are URLs rewritten by security solutions to enable additional analysis when the URL is clicked. Once analyzed, they may prompt a user, redirect the browser back to the original URL, or block further access if deemed necessary.
What is Safelink Smuggling?
Safelink Smuggling is a technique that involves an attacker purposely getting their malicious payload rewritten by a security solution’s Safelink capability to then propagate the rewritten URL to others. This technique is a way for attackers to not only avoid detection by traditional email security and other solutions, but also to instill mistrust in all email security solutions. As a result, Safelinks from a range of popular email security providers are often seen in phishing or supply chain attacks. In fact, Darktrace has observed over 300,000 cases of Safelinks being included in unexpected and suspicious contexts over the last 3 months.
How does Safelink Smuggling work?
Safelink Smuggling has two key stages: Getting a malicious link rewritten by an email security solution, then propagating that rewritten link to other victims.
Step one:
Obfuscated a malicious payload through a Safelink capability rewriting the link; Darktrace has seen this attempted through two methods – Compromised Account or Reply-Chain.
- Method 1: Compromised Account
If an attacker can gain access to a compromised account – whether that’s through brute force, malware or credential theft – they can infiltrate it with malicious links, and then exfiltrate the Safelinks created as the email passes through security filtering. In other words, attackers will send a malicious payload to the compromised inbox, with the intent that the malicious URL gets rewritten. Unlike a normal phishing email where the threat actor wants to avoid having their email blocked, in this case the objective is for the email to get through to the inbox with the link rewritten. As observed by Darktrace, attackers often send the link in isolation as any additional components (i.e., body text or other content in the email) could cause a more severe action such as the email security solution holding the message.
- Method 2: Reply-Chain
With this method, the attacker sends a malicious link to an email security vendor’s customer in an attempt to solicit a reply from an internal user. This allows them to grab the re-written URL within the reply chain. However, this is a risky tactic which can fail at several points. The attacker has to be confident the initial email won't be blocked outright; they also risk alerting security vendors to the address and the URL intended to be used for the main campaign. They also must be confident that the checks made when the re-written URL is clicked will not lead to a block at the final destination.
Regardless of the method used, the end result will appear as follows:
For example, the original malicious URL may look like this,
faceldu[.]org/Invoice112.zip
(negative surface indicators: recently registered domain, file extension)
And after being rewritten,
securityvevndor[.]com/safe?q=aNDF80dfaAkAH930adbd
(positive surface indicators: established domain, positive reputation, associated with safe content)
Step Two:
Now that the attacker has access to a malicious URL that has been obfuscated by a safe rewrite, attackers can forward or craft an email leveraging that same link. In fact, we have even seen multiple layers of Safelink Smuggling being used to mask a payload further.
The Challenge of Link Rewriting
Traditional email security solutions rewrite all links sent to an organization, but there is an inherent risk to this methodology. Rewriting every link, whether harmless or harmful, leads employees to lose context and creates a false sense of security when interacting with rewritten links in emails. Furthermore, it provides attackers with many opportunities to exploit Safelinks. As demonstrated in Method 2 above, if an email security solution does not rewrite every link, executing such attacks would be significantly more challenging.
Traditionally, rewriting every link made sense from a security perspective, as it allowed servers to thoroughly analyze links for known attack patterns and signatures. However, this approach relies on identifying previously recognized threats. Conversely, Darktrace / EMAIL gathers sufficient information about a link without needing to rewrite it, by analyzing the context and content of the email and the link itself.
In fact, Darktrace is the pioneer in applying selective rewriting to URLs based on suspicious properties or context, a method that other solutions have since adopted. While traditional solutions rewrite links to assess them only after they are clicked, Darktrace / EMAIL takes immediate action to neutralize threats before they reach the inbox.
Darktrace achieves high success rates in detecting malicious links and emails on the first encounter using Self-Learning AI. By understanding 'normal' behavior in email communications, Darktrace identifies subtle deviations indicative of cyber threats and selectively rewrites only those links deemed suspicious, ensuring a targeted, proportionate, and non-disruptive response.
Why do traditional email security solutions miss Safelink attacks?
Traditional security solutions that focus on learning attack patterns will miss Safelink threats as they are often utilized in attacks that have a variety of layers which help the email seem legitimate. Leveraging all the classic techniques seen in a supply chain attack to disguise the sender's intent, taking advantage of the users' inherent trust in familiar sources, the user is more likely to lower their defenses.
For more information: https://darktrace.com/products/email/use-cases/supply-chain-attack
In terms of the URL, if the payload is malicious, why is it difficult for email security solutions to catch it? Primarily, other security vendors will focus on the payload in isolation, attempting to find known attack patterns or signatures such as a domain name or IP with a bad reputation. Unfortunately, with this technique, if the URL has a legitimate domain, it will return a clean track record. Common obfuscation techniques such as captchas, short-links, and click throughs can all be deployed to add layers of complexity to the analysis.
Safelink Smuggling relies heavily on link redirects, which means that web analysis tools will falter as they will only analyze the first redirect. Consequently, when more in-depth analysis on the link itself is performed, the first place the URL takes the user is not the malicious site but rather the default on-click analysis of the vendor in question. Therefore, any traditional browser or link analysis will also return a negative result.
Finally, the context itself is important. In contrast to traditional email security solutions, Darktrace / EMAIL asks who, what, when, where, and why for every single email, and compares it to the pattern of life of both the internal recipient and the external sender, rather than attempting to match patterns with historical threat data. When analyzing an email from an inbound perspective, Darktrace reveals potential deviations from normal, that, when considered sufficiently anomalous, will result in taking a proportional action to the threat assessed.
To illustrate the above, let’s take a look at an example email that Darktrace recently caught.
The following is an email a Darktrace customer received, which Darktrace / EMAIL held before it reached the inbox. In this case, the smuggled Safelink was further obfuscated behind a QR Code. The accompanying document also presented some anomalies in terms of its intent, perceived as a potential social engineering attempt. Finally, the lack of association and low mailing history meant there was no prior context for this email.

How to mitigate against Safelink Smuggling?
It's difficult for email security vendors to do anything about their links being reused, and reuse should almost be expected by popular operators in the email security space. Therefore, the presence of links from a vendor’s domain in a suspicious email communication rarely indicates a compromise of the link rewrite infrastructure or a compromise of the third-party vendor.
Email security vendors can improve their defense-in-depth, especially around their email provider accounts to avoid Method 1 (Compromised Account attacks) and become more selective with their rewrites to curtail Method 2 (Reply Chain attacks).
Primary protection against Safelink Smuggling should be offered by the email security vendor responsible for inbound email analysis. They need to ensure that techniques such as Safelink Smuggling are not evaded by their detection mechanisms.
Darktrace has long been working on the betterment of security within the email community and innovating our link analysis infrastructure to mitigate against this attack methodology (read more about our major update in 6.2 here), regardless of whether the receiving organization are Darktrace customers.
How does Darktrace deal with Safelink Smuggling today?
Darktrace has been dealing with Safelink Smuggling since launch and has a standardized recommendation for customers who are looking to defend against this threat.
Customers want to avoid being 1) the propagators of this threat and potentially damaging their brand reputation, and 2) being victims of the supply chain attack thereafter.
The principal recommendation to protect customer accounts and consequently their brands is to ensure defense-in-depth. As accounts establish themselves as the crown jewels of any modern enterprise, organizations should vigilantly monitor their account activity with the same rigor they would analyze their network activity. Whether that is through the base account takeover protection offered by Darktrace / EMAIL, or the expanded defense offered by Darktrace / IDENTITY, it is crucial that the accounts themselves have a robust security solution in place.
Secondly, to avoid falling victim to the supply chain attack that leverages a third-party vendor’s link rewrite, it is imperative to use a solution that does not rely on static threat intelligence and link reputation analysis. Rather than chasing attackers by updating rules and signatures, Darktrace leverages Self-Learning AI to learn the communication patterns of both internal and external messages to reveal deviations in both content and context.
Finally, for those customers that already leverage Darktrace / EMAIL we recommend ensuring that lock links are enabled, and that the default warning page is displayed every time a link is rewritten, no matter the perceived severity of the link. This will allow any potential user that clicks on a rewritten Darktrace / EMAIL link to be alerted to the potential nature of the site they are trying to access.
Safelink smuggling example caught by Darktrace
While most cases involve other vendors, analysts recently saw a case where Darktrace's own links were used in this type of attack. A small number of links were leveraged in a campaign targeting both Darktrace and non-Darktrace customers alike. Thankfully, these attempts were all appropriately actioned by those customers that had Darktrace / EMAIL deployed.
In the example below, you will see how Darktrace Cyber AI Analyst describes the example at hand under the Anomaly Indicators section.

First, the display name mismatch can be interpreted as an indicator of social engineering, attempting to deceive the recipient with an IT policy change.
Second, the link itself, which in this case is a hidden redirect to an unusual host for this environment.
Finally, there is a suspected account takeover due to the origin of the email being a long-standing, validated domain that contains a wide variety of suspicious elements.
Darktrace / EMAIL would have held this email from being delivered.
Conclusion
By investigating Safelink Smuggling, Darktrace wants to shine a light on the technique for security teams and help raise awareness of how it can be used to dupe users into lowering their defenses. Challenge your email security vendor on how it deals with link analysis, particularly from trusted senders and applications.
Interested in Darktrace’s approach to defense-in-depth? Check out Darktrace / EMAIL