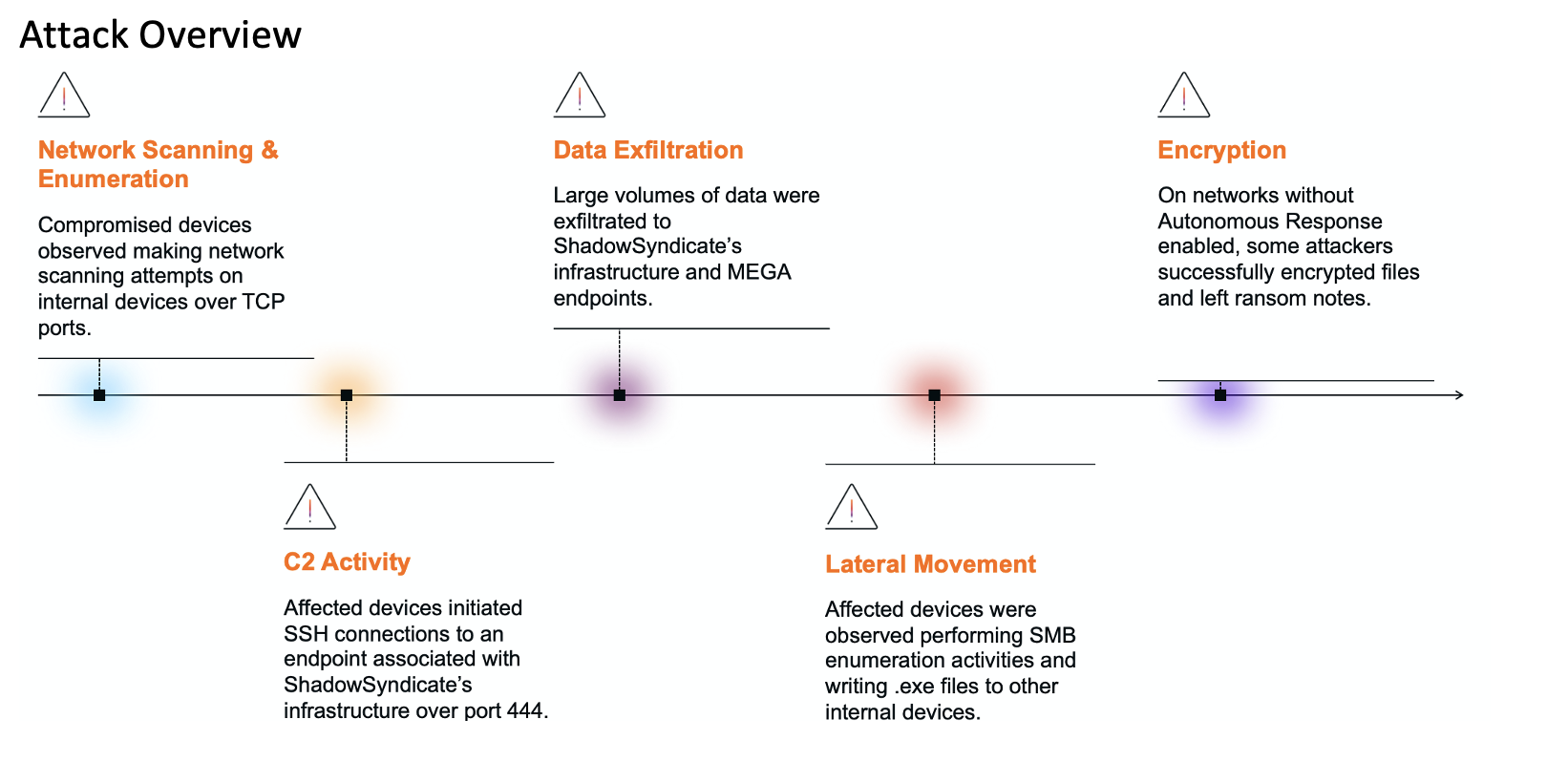
In December 2021 several CVEs[1] were issued for the Log4j vulnerabilities that sent security teams into a global panic. Threat actors are now continuously scanning external infrastructure for evidence of the vulnerability to deploy crypto-mining malware.[2] However, through December ‘21 – February ‘22, it was ransomware groups that seized the initiative.
Compromise
In January 2022, a Darktrace customer left an external-facing VMware server unpatched allowing Cobalt Strike to be successfully installed. Several IoCs indicate that Cuba Ransomware operators were behind the attack. Thanks to the Darktrace SOC service, the customer was notified of the active threat on their network, and Antigena’s Autonomous Response was able to keep the attackers at bay before encryption events took place.
Initially the VMware server breached two models relating to an anomalous script download and a new user agent both connecting via HTTP. As referenced in an earlier Darktrace blog, both of these models had been seen in previous Log4j exploits. As with all Darktrace models however, the model deck is not designed to detect only one exploit, infection variant, or APT.

Figure 1: Darktrace models breaching due to the malicious script download
Analyst investigation
A PCAP of the downloaded script showed that it contained heavily obfuscated JavaScript. After an OSINT investigation a similar script was uncovered which likely breached the same Yara rules.

Figure 2: PCAP of the Initial HTTP GET request for the Windows Script component

Figure 3: PCAP of the initial HTTP response containing obfuscated JavaScript

Figure 4: A similar script that has been observed installing additional payloads after an initial infection[3]
While not an exact match, this de-obfuscated code shared similarities to those seen when downloading other banking trojans.
Having identified on the Darktrace UI that this was a VMware server, the analyst isolated the incoming external connections to the server shortly prior to the HTTP GET requests and was able to find an IP address associated with Log4j exploit attempts.

Figure 5: Advanced Search logs showing incoming SSL connections from an IP address linked to Log4j exploits
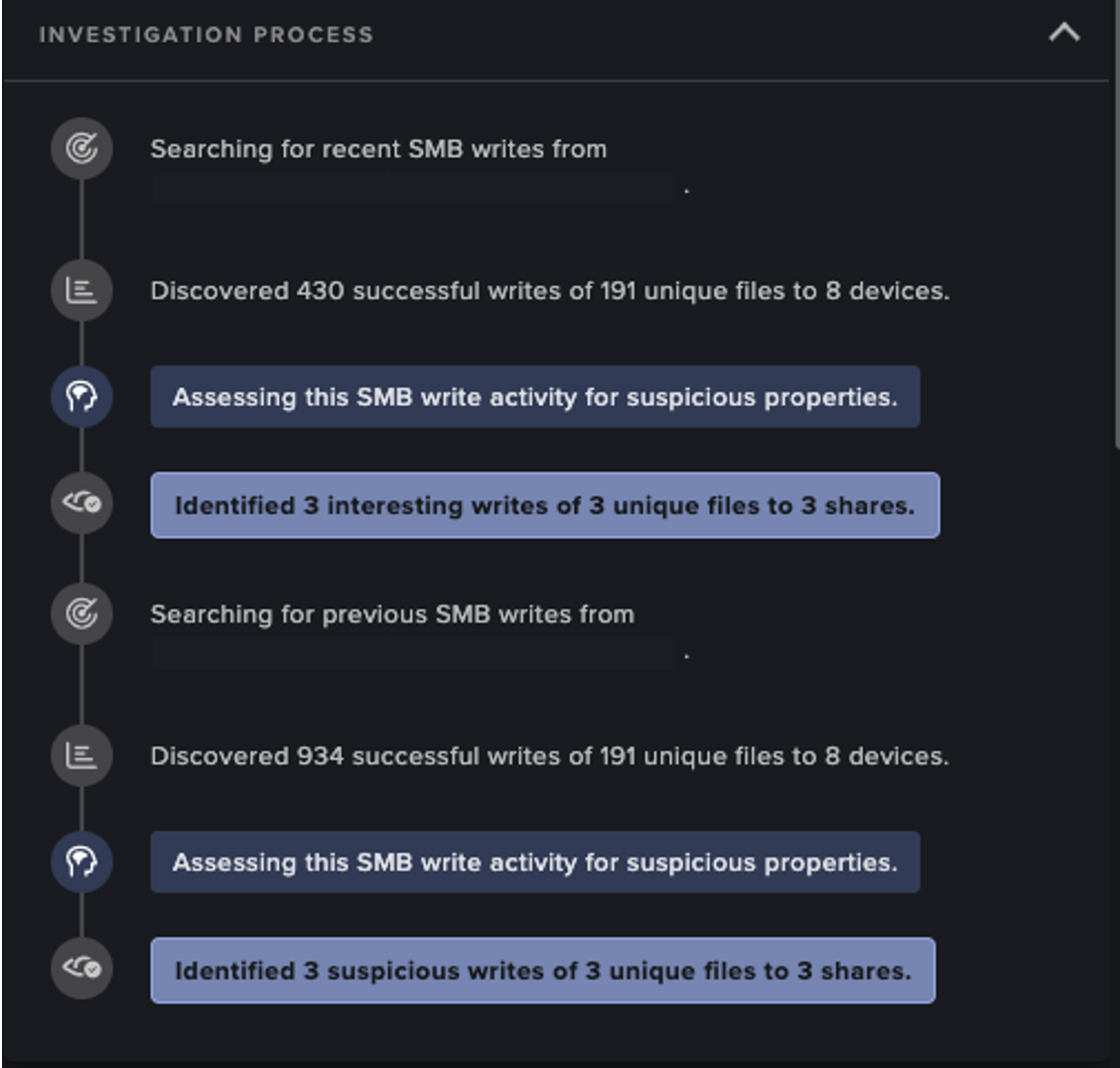
Through Advanced Search the analyst identified spikes shortly prior and immediately after the download. This suggested the files were downloaded and executed by exploiting the Log4j vulnerability.
Antigena response

Figure 6: AI Analyst reveals both the script downloads and the unusual user agent associated with the connections

Figure 7: Antigena blocked all further connections to these endpoints following the downloads
Cobalt Strike
Cobalt Strike is a popular tool for threat actors as it can be used to perform a swathe of MITRE ATT&CK techniques. In this case the threat actor attempted command and control tactics to pivot through the network, however, Antigena responded promptly when the malware attempted to communicate with external infrastructure.
On Wednesday January 26, the DNS beacon attempted to connect to malicious infrastructure. Antigena responded, and a Darktrace SOC analyst issued an alert.

Figure 8: A Darktrace model detected the suspicious DNS requests and Antigena issued a response
The attacker changed their strategy by switching to a different server “bluetechsupply[.]com” and started issuing commands over TLS. Again, Darktrace detected these connections and AI Analyst reported on the incident (Figure 9, below). OSINT sources subsequently indicated that this destination is affiliated with Cobalt Strike and was only registered 14 days prior to this incident.

Figure 9: AI Analyst summary of the suspicious beaconing activity
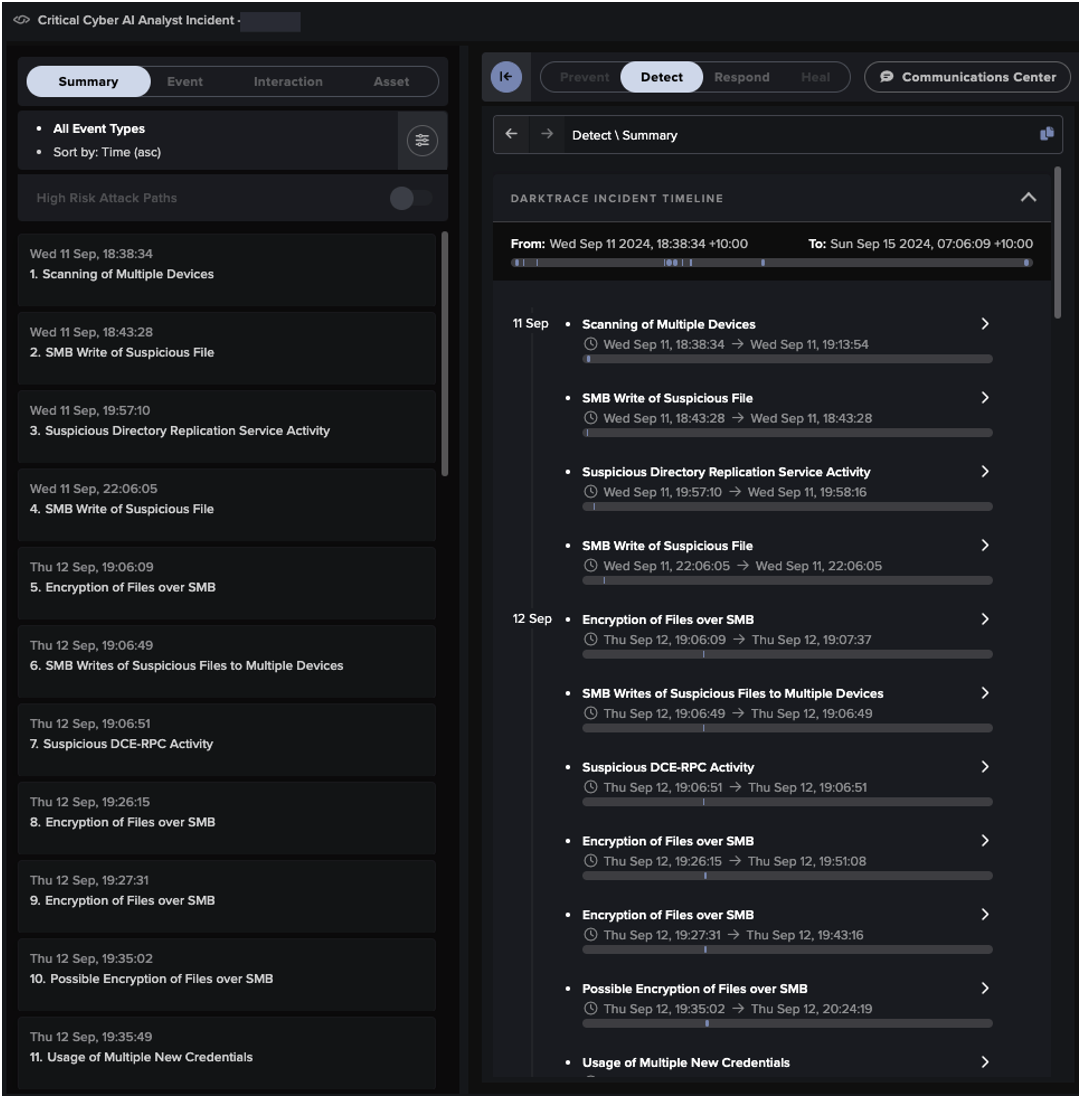
Simultaneous to these connections, the device scanned multiple internal devices via an ICMP scan and then scanned the domain controller over key TCP ports including 139 and 445 (SMB). This was followed by an attempt to write an executable file to the domain controller. While Antigena intervened in the file write, another Darktrace SOC analyst was issuing an alert due to the escalation in activity.

Figure 10: AI Analyst summary of the .dll file that Antigena intercepted to the Windows/temp directory of the domain controller
Following the latest round of Antigena blocks, the threat actor attempted to change methods again. The VMware server utilised the Remote Access Tool/Trojan NetSupport Manager in an attempt to install further malware.

Figure 11: Darktrace reveals the attacker changing tactics
Despite this escalation, Darktrace yet again blocked the connection.
Perhaps due to an inability to connect to C2 infrastructure, the attack stopped in its tracks for around 12 hours. Thanks to Antigena and the Darktrace SOC team, the security team had been afforded time to remediate and recover from the active threat in their network. Interestingly, Darktrace detected a final attempt at pivoting from the machine, with an unusual PowerShell Win-RM connection to an internal machine. The modern Win-RM protocol typically utilises port 5985 for HTTP connections however pre-Windows 7 machines may use Windows 7 indicating this server was running an old OS.

Figure 12: Darktrace detects unusual PowerShell usage
Cuba Ransomware
While no active encryption appears to have taken place for this customer, a range of IoCs were identified which indicated that the threat actor was the group being tracked as UNC2596, the operators of Cuba Ransomware.[4]
These IoCs include: one of the initially dropped files (komar2.ps1,[5] revealed by AI Analyst in Figure 6), use of the NetSupport RAT,[6] and Cobalt Strike beaconing.[7] These were implemented to maintain persistence and move laterally across the network.
Cuba Ransomware operators prefer to exfiltrate data to their beacon infrastructure rather than using cloud storage providers, however no evidence of upload activity was observed on the customer’s network.
Concluding thoughts
Unpatched, external-facing VMware servers vulnerable to the Log4j exploit are actively being targeted by threat actors with the aim of ransomware detonation. Without using rules or signatures, Darktrace was able to detect all stages of the compromise. While Antigena delayed the attack, forcing the threat actor to change C2 servers constantly, the Darktrace analyst team relayed their findings to the security team who were able to remediate the compromised machines and prevent a final ransomware payload from detonating.
For Darktrace customers who want to find out more about Cobalt Strike, refer here for an exclusive supplement to this blog.
Appendix
Darktrace model detections
Initial Compromise:
- Device / New User Agent To Internal Server
- Anomalous Server Activity / New User Agent from Internet Facing System
- Experimental / Large Number of Suspicious Successful Connections
Breaches from Critical Devices / DC:
- Device / Large Number of Model Breaches
- Antigena / Network / External Threat / Antigena File then New Outbound Block
- Device / SMB Lateral Movement
- Experimental / Unusual SMB Script Write V2
- Compliance / High Priority Compliance Model Breach
- Anomalous Server Activity / Anomalous External Activity from Critical Network Device
- Experimental / Possible Cobalt Strike Server IP V2
Lateral Movement:
- Antigena / Network / Insider Threat / Antigena Internal Anomalous File Activity
- Compliance / SMB Drive Write
- Anomalous File / Internal / Executable Uploaded to DC
- Experimental / Large Number of Suspicious Failed Connections
- Compromise / Suspicious Beaconing Behaviour
- Antigena / Network / Significant Anomaly / Antigena Breaches Over Time Block
- Antigena / Network / External Threat / Antigena Suspicious Activity Block
- Anomalous Connection / High Volume of Connections to Rare Domain
- Antigena / Network / Significant Anomaly / Antigena Enhanced Monitoring from Server Block
Network Scan Activity:
- Device / Suspicious SMB Scanning Activity
- Experimental / Network Scan V2
- Device / ICMP Address Scan
- Experimental / Possible SMB Scanning Activity
- Experimental / Possible SMB Scanning Activity V2
- Antigena / Network / Insider Threat / Antigena Network Scan Block
- Device / Network Scan
- Compromise / DNS / Possible DNS Beacon
- Device / Internet Facing Device with High Priority Alert
- Antigena / Network / Significant Anomaly / Antigena Enhanced Monitoring from Server Block
DNS / Cobalt Strike Activity:
- Experimental / Possible Cobalt Strike Server IP
- Experimental / Possible Cobalt Strike Server IP V2
- Antigena / Network / External Threat / Antigena File then New Outbound Block
- Antigena / Network / External Threat / Antigena Suspicious File Block
- Anomalous Connection / New User Agent to IP Without Hostname
- Anomalous File / Script from Rare External Location
MITRE ATT&CK techniques observed

IoCs

Thanks to Brianna Leddy, Sam Lister and Marco Alanis for their contributions.
Footnotes
1.
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44228
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44530
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-45046
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-4104
2. https://www.toolbox.com/it-security/threat-reports/news/log4j-vulnerabilities-exploitation-attempts
3. https://twitter.com/ItsReallyNick/status/899845845906071553
4. https://www.mandiant.com/resources/unc2596-cuba-ransomware
5. https://www.ic3.gov/Media/News/2021/211203-2.pdf
6. https://threatpost.com/microsoft-exchange-exploited-cuba-ransomware/178665/
7. https://www.bleepingcomputer.com/news/security/microsoft-exchange-servers-hacked-to-deploy-cuba-ransomware/
8. https://gist.github.com/blotus/f87ed46718bfdc634c9081110d243166