How does Loader Malware work?
Throughout 2023, the Darktrace Threat Research team identified and investigated multiple strains of loader malware affecting customers across its fleet. These malicious programs typically serve as a gateway for threat actors to gain initial access to an organization’s network, paving the way for subsequent attacks, including additional malware infections or disruptive ransomware attacks.
How to defend against loader malware
The prevalence of such initial access threats highlights the need for organizations to defend against multi-phase compromises, where modular malware swiftly progresses from one stage of an attack to the next. One notable example observed in 2023 was Pikabot, a versatile loader malware used for initial access and often accompanied by secondary compromises like Cobalt Strike and Black Basta ransomware.
While Darktrace initially investigated multiple instances of campaign-like activity associated with Pikabot during the summer of 2023, a new campaign emerged in October which was observed targeting a Darktrace customer in Europe. Thanks to the timely detection by Darktrace DETECT™ and the support of Darktrace’s Security Operations Center (SOC), the Pikabot compromise was quickly shut down before it could escalate into a more disruptive attack.
What is Pikabot?
Pikabot is one of the latest modular loader malware strains that has been active since the first half of 2023, with several evolutions in its methodology observed in the months since. Initial researchers noted similarities to the Qakbot aka Qbot or Pinkslipbot and Mantanbuchus malware families, and while Pikabot appears to be a new malware in early development, it shares multiple commonalities with Qakbot [1].
First, both Pikabot and Qakbot have similar distribution methods, can be used for multi-stage attacks, and are often accompanied by downloads of Cobalt Strike and other malware strains. The threat actor known as TA577, which has also been referred to as Water Curupira, has been seen to use both types of malware in spam campaigns which can lead to Black Basta ransomware attacks [2] [3].Notably, a rise in Pikabot campaigns were observed in September and October 2023, shortly after the takedown of Qakbot in Operation Duck Hunt, suggesting that Pikabot may be serving as a replacement for initial access to target network [4].
How does Pikabot malware work?
Many Pikabot infections start with a malicious email, particularly using email thread hijacking; however, other cases have been distributed via malspam and malvertising [5]. Once downloaded, Pikabot runs anti-analysis techniques and checks the system’s language, self-terminating if the language matches that of a Commonwealth of Independent States (CIS) country, such as Russian or Ukrainian. It will then gather key information to send to a command-and-control (C2) server, at which point additional payload downloads may be observed [2]. Early response to a Pikabot infection is important for organizations to prevent escalation to a significant compromise such as ransomware.
Darktrace’s Coverage of Pikabot malware
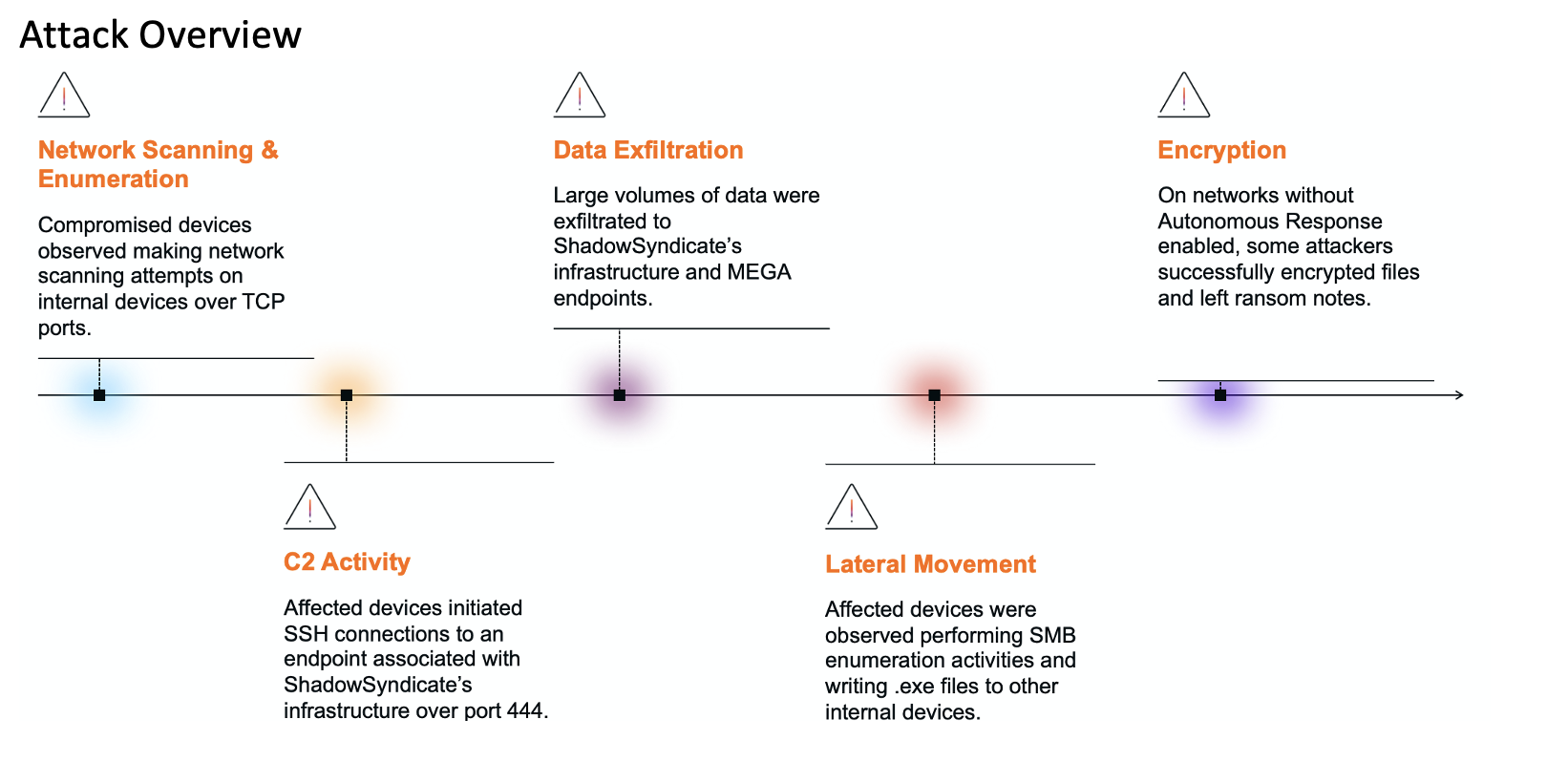
Between April and July 2023, the Darktrace Threat Research team investigated Pikabot infections affected more than 15 customer environments; these attacks primarily targeted US and European organizations spanning multiple industries, and most followed the below lifecycle:
- Initial access via malspam or email, often outside of Darktrace’s scope
- Suspicious executable download from a URI in the format /\/[a-z0-9A-Z]{3,}\/[a-z0-9A-Z]{5,}/ and using a Windows PowerShell user agent
- C2 connections to IP addresses on uncommon ports including 1194 and 2078
- Some cases involved further C2 activity to Cobalt Strike endpoints
In October 2023, a second campaign emerged that largely followed the same attack pattern, with a notable difference that cURL was used for the initial payload download as opposed to PowerShell. All the Pikabot cases that Darktrace has observed since October 2023 have used cURL, which could indicate a shift in approach from targeting Windows devices to multi-operating system environments.

On October 17, 2023, Darktrace observed a Pikabot infection on the network of a European customer after an internal user seemingly clicked a malicious link in a phishing email, thereby compromising their device. As the customer did not have Darktrace/Email™ deployed on their network, Darktrace did not have visibility over the email. Despite this, DETECT was still able to provide full visibility over the network-based activity that ensued.
Darktrace observed the device using a cURL user agent when initiating the download of an unusual executable (.exe) file from an IP address that had never previously been observed on the network. Darktrace further recognized that the executable file was attempting to masquerade as a different file type, likely to evade the detection of security teams and their security tools. Within one minute, the device began to communicate with additional unusual IP addresses on uncommon ports (185.106.94[.]174:5000 and 80.85.140[.]152:5938), both of which have been noted by open-source intelligence (OSINT) vendors as Pikabot C2 servers [6] [7].

Around 40 minutes after the initial download, Darktrace detected the device performing suspicious DNS tunneling using a pattern that resembled the Cobalt Strike Beacon. This was accompanied by beaconing activity to a rare domain, ‘wordstt182[.]com’, which was registered only 4 days prior to this activity [8]. Darktrace observed additional DNS connections to the endpoint, ‘building4business[.]net’, which had been linked to Black Basta ransomware [2].

As this customer had integrated Darktrace with the Microsoft Defender, Defender was able to contextualize the DETECT model breaches with endpoint insights, such as known threats and malware, providing customers with unparalleled visibility of the host-level detections surrounding network-level anomalies.
In this case, the behavior of the affected device triggered multiple Microsoft Defender alerts, including one alert which linked the activity to the threat actor Storm-0464, another name for TA577 and Water Curupira. These insights were presented to the customer in the form of a Security Integration alert, allowing them to build a full picture of the ongoing incident.

As the customer had subscribed to Darktrace’s Proactive Threat Notification (PTN) service, the customer received timely alerts from Darktrace’s SOC notifying them of the suspicious activity associated with Pikabot. This allowed the customer’s security team to quickly identify the affected device and remove it from their environment for remediation.
Although the customer did have Darktrace RESPOND™ enabled on their network, it was configured in human confirmation mode, requiring manual application for any RESPOND actions. RESPOND had suggested numerous actions to interrupt and contain the attack, including blocking connections to the observed Pikabot C2 addresses, which were manually actioned by the customer’s security team after the fact. Had RESPOND been enabled in autonomous response mode during the attack, it would have autonomously blocked these C2 connections and prevented the download of any suspicious files, effectively halting the escalation of the attack.
Nonetheless, Darktrace DETECT’s prompt identification and alerting of this incident played a crucial role in enabling the customer to mitigate the threat of Pikabot, preventing it from progressing into a disruptive ransomware attack.

Conclusion
Pikabot is just one recent example of a modular strain of loader known for its adaptability and speed, seamlessly changing tactics from one campaign to the next and utilizing new infrastructure to initiate multi-stage attacks. Leveraging commonly used tools and services like Windows PowerShell and cURL, alongside anti-analysis techniques, this malware can evade the detection and often bypass traditional security tools.
In this incident, Darktrace detected a Pikabot infection in its early stages, identifying an anomalous file download using a cURL user agent, a new tactic for this particular strain of malware. This timely detection, coupled with the support of Darktrace’s SOC, empowered the customer to quickly identify the compromised device and act against it, thwarting threat actors attempting to connect to malicious Cobalt Strike and Black Basta servers. By preventing the escalation of the attack, including potential ransomware deployment, the customer’s environment remained safeguarded.
Had Darktrace RESPOND been enabled in autonomous response mode at the time of this attack, it would have been able to further support the customer by applying targeted mitigative actions to contain the threat of Pikabot at its onset, bolstering their defenses even more effectively.
Credit to Brianna Leddy, Director of Analysis, Signe Zaharka, Senior Cyber Security Analyst
Appendix
Darktrace DETECT Models
Anomalous Connection / Anomalous SSL without SNI to New External
Anomalous Connection / Application Protocol on Uncommon Port
Anomalous Connection / Multiple Connections to New External TCP Port
Anomalous Connection / New User Agent to IP Without Hostname
Anomalous Connection / Powershell to Rare External
Anomalous Connection / Rare External SSL Self-Signed
Anomalous Connection / Repeated Rare External SSL Self-Signed
Anomalous File / EXE from Rare External Location
Anomalous File / Masqueraded File Transfer
Anomalous File / Multiple EXE from Rare External Locations
Compromise / Agent Beacon to New Endpoint
Compromise / Beacon to Young Endpoint
Compromise / Beaconing Activity To External Rare
Compromise / DNS / DNS Tunnel with TXT Records
Compromise / New or Repeated to Unusual SSL Port
Compromise / SSL Beaconing to Rare Destination
Compromise / Suspicious Beaconing Behaviour
Compromise / Suspicious File and C2
Device / Initial Breach Chain Compromise
Device / Large Number of Model Breaches
Device / New PowerShell User Agent
Device / New User Agent
Device / New User Agent and New IP
Device / Suspicious Domain
Security Integration / C2 Activity and Integration Detection
Security Integration / Egress and Integration Detection
Security Integration / High Severity Integration Detection
Security Integration / High Severity Integration Incident
Security Integration / Low Severity Integration Detection
Security Integration / Low Severity Integration Incident
Antigena / Network / External Threat / Antigena File then New Outbound Block
Antigena / Network / External Threat / Antigena Suspicious Activity Block
Antigena / Network / External Threat / Antigena Suspicious File Block
Antigena / Network / Significant Anomaly / Antigena Breaches Over Time Block
Antigena / Network / Significant Anomaly / Antigena Controlled and Model Breach
Antigena / Network / Significant Anomaly / Antigena Enhanced Monitoring from Client Block
Antigena / Network / Significant Anomaly / Antigena Significant Anomaly from Client Block
Antigena / Network / Significant Anomaly / Antigena Significant Security Integration and Network Activity Block
List of Indicators of Compromise (IoC)
IOC - TYPE - DESCRIPTION + CONFIDENCE
128.140.102[.]132 - IP Address - Pikabot Download
185.106.94[.]174:5000 - IP Address: Port - Pikabot C2 Endpoint
80.85.140[.]152:5938 - IP Address: Port - Pikabot C2 Endpoint
building4business[.]net - Hostname - Cobalt Strike DNS Beacon
wordstt182[.]com - Hostname - Cobalt Strike Server
167.88.166[.]109 - IP Address - Cobalt Strike Server
192.9.135[.]73 - IP - Pikabot C2 Endpoint
192.121.17[.]68 - IP - Pikabot C2 Endpoint
185.87.148[.]132 - IP - Pikabot C2 Endpoint
129.153.22[.]231 - IP - Pikabot C2 Endpoint
129.153.135[.]83 - IP - Pikabot C2 Endpoint
154.80.229[.]76 - IP - Pikabot C2 Endpoint
192.121.17[.]14 - IP - Pikabot C2 Endpoint
162.252.172[.]253 - IP - Pikabot C2 Endpoint
103.124.105[.]147 - IP - Likely Pikabot Download
178.18.246[.]136 - IP - Pikabot C2 Endpoint
86.38.225[.]106 - IP - Pikabot C2 Endpoint
198.44.187[.]12 - IP - Pikabot C2 Endpoint
154.12.233[.]66 - IP - Pikabot C2 Endpoint
MITRE ATT&CK Mapping
TACTIC - TECHNIQUE
Defense Evasion - Masquerading: Masquerade File Type (T1036.008)
Command and Control - Application Layer Protocol: Web Protocols (T1071.001)
Command and Control - Non-Standard Port (T1571)
Command and Control - Application Layer Protocol: DNS (T1071.004)
Command and Control - Protocol Tunneling (T1572)
References
[1] https://news.sophos.com/en-us/2023/06/12/deep-dive-into-the-pikabot-cyber-threat/?&web_view=true
[2] https://www.trendmicro.com/en_be/research/24/a/a-look-into-pikabot-spam-wave-campaign.html
[3] https://thehackernews.com/2024/01/alert-water-curupira-hackers-actively.html
[5] https://www.redpacketsecurity.com/pikabot-distributed-via-malicious-ads-6/
[6] https://www.virustotal.com/gui/ip-address/185.106.94.174/detection
[7] https://www.virustotal.com/gui/ip-address/80.85.140.152/detection