What is Email Spam?
Email Spam Overview
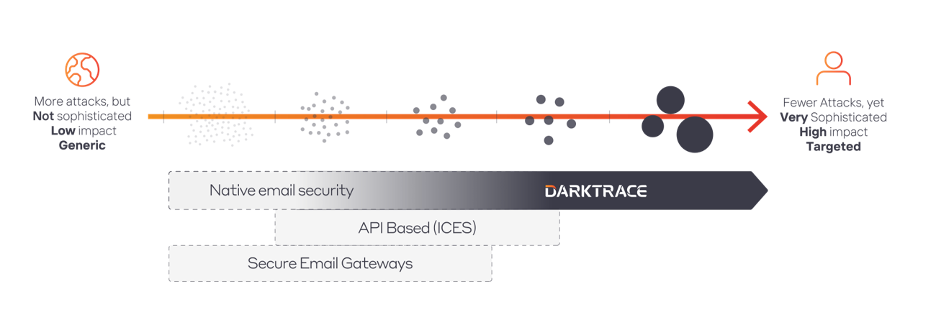
Spam messages are not just annoying inbox clutter, they can range from benign advertisements to significant security threats. Despite sophisticated email spam protection, some spam cleverly bypasses these defenses, sometimes being flagged as “High Priority” with urgent icons. This article delves into the different types of spam and the associated risks in spam cybersecurity.
Email spam definition
Email spam includes unwanted or unsolicited emails that arrive in a user’s email inbox. Usually, email spam is sent to a large number of recipients. Spam can be sent automatically by a botnet or by human senders.
If spam is not appropriately dealt with it can become troublesome for users to conduct work activity without disruption from unwanted emails. Email spam also poses a security threat because messages can contain malicious links or malware that can allow a cyber-criminal access to a user’s device or ability to find sensitive data/account information.
How does spam email work?
The method of spamming has been around for quite some time and since then has become a common method of cyber disruption. To launch an email spam attack, a cyber-criminal will use spambots, computer systems that conduct repetitive tasks designed to assist in spamming activities, to gather emails available on the internet and send out a large amount malicious emails. Spam emails use a “spray and pray” tactic which involves sending spam emails in masses with hopes that a few individuals will mistakenly interact with the spam content.
The simplicity and minimal cost of sending spam messages make this practice a persistently effective method of cyber disruption. Using basic tools like Microsoft Word, one can quickly format and dispatch millions of emails, potentially yielding substantial profits. This highlights a crucial aspect of spam cybersecurity and underscores the importance of email spam protection.
How do spammers find my email?
Email addresses are harvested from places like newsgroups and chat rooms where users might inadvertently reveal their contact details. Spambots, specialized software designed for finding this information, scan these forums and webpages looking for the "@" sign, identifying potential spam targets.
Furthermore, deceptive websites promising lucrative prizes in exchange for email addresses, and even dictionary attacks on large email servers, like those of MSN or AOL, are common techniques. A dictionary attack involves systematically guessing email addresses and checking them against a server to determine which ones are active.
Once acquired, these email addresses often get marked as spam when circulated among different spammers, contributing to the volume of unwanted messages recipients face. This relentless sharing and utilization of email addresses in the spam ecosystem necessitates heightened security awareness and robust spam filters.
This deep dive into the types of spam and the methods used for its dissemination enhances our understanding of what is spam in cybersecurity, highlighting the crucial need for effective strategies to mitigate these risks, employing both technological defenses and informed user practices.
Different types of spam
Commercial Advertisements
Many commercial emails fall under the category of spam, yet they must adhere to the CAN-SPAM Act's regulations in the United States. When companies acquire your email through online forms, they often automatically sign you up for newsletters as an economical marketing strategy. To avoid unwanted emails, always check for an opt-in checkbox when providing your email. Legally, these messages should include a clear way to unsubscribe. If unsubscribing fails, consider adjusting your email settings to block further messages from that sender.
Antivirus Warnings
A typical spam email tactic involves fake antivirus alerts. These emails claim your computer is at risk and offer a link to perform an antivirus scan. However, clicking these links can compromise your system by installing malware or granting hackers access. If you receive such a warning and suspect an infection, ignore the email and instead opt for reputable cybersecurity software to secure your device.
Email Spoofing
Phishing scams are often successful because they expertly mimic legitimate corporate communications to provoke a response. In an email spoofing attack, spammers choose a trustworthy company brand, replicating its official format and logos to deceive you. Always verify the sender's actual email address (not just the display name) in the From line before responding or clicking on anything. When in doubt, directly contact the company to confirm the authenticity of the email.
Sweepstakes Winners
Emails claiming you've won a sweepstakes or prize are commonly sent by spammers to elicit a quick response. These emails might urge you to click a link or submit personal information to claim your winnings. If the competition is unfamiliar or the email looks suspicious, refrain from interacting with the link or providing any personal details.
Money Scams
Spammers often exploit people's generosity with emails that narrate urgent, fictitious situations requiring financial help. Common schemes promise significant returns if you provide bank details or pay a nominal fee. Always exercise caution before sharing personal information or sending money based on email requests.
How to identify spam emails
Certain characteristics of an email will reveal to a user that it is spam. Here is what to look for:
Sender credentials
check the sender of any unsolicited email to make sure that it is coming from a legitimate source.
Subject line
Spam emails will have vague subject lines or ones that attempt to alarm or call for urgent action. This might come in the form of an alert or a fraudulent notification that your “account” is closing.
Requesting information
Spam emails are always trying to divulge sensitive information from their victims. Never share your personal account information unless you are 100% certain of the senders identity.
For organizations
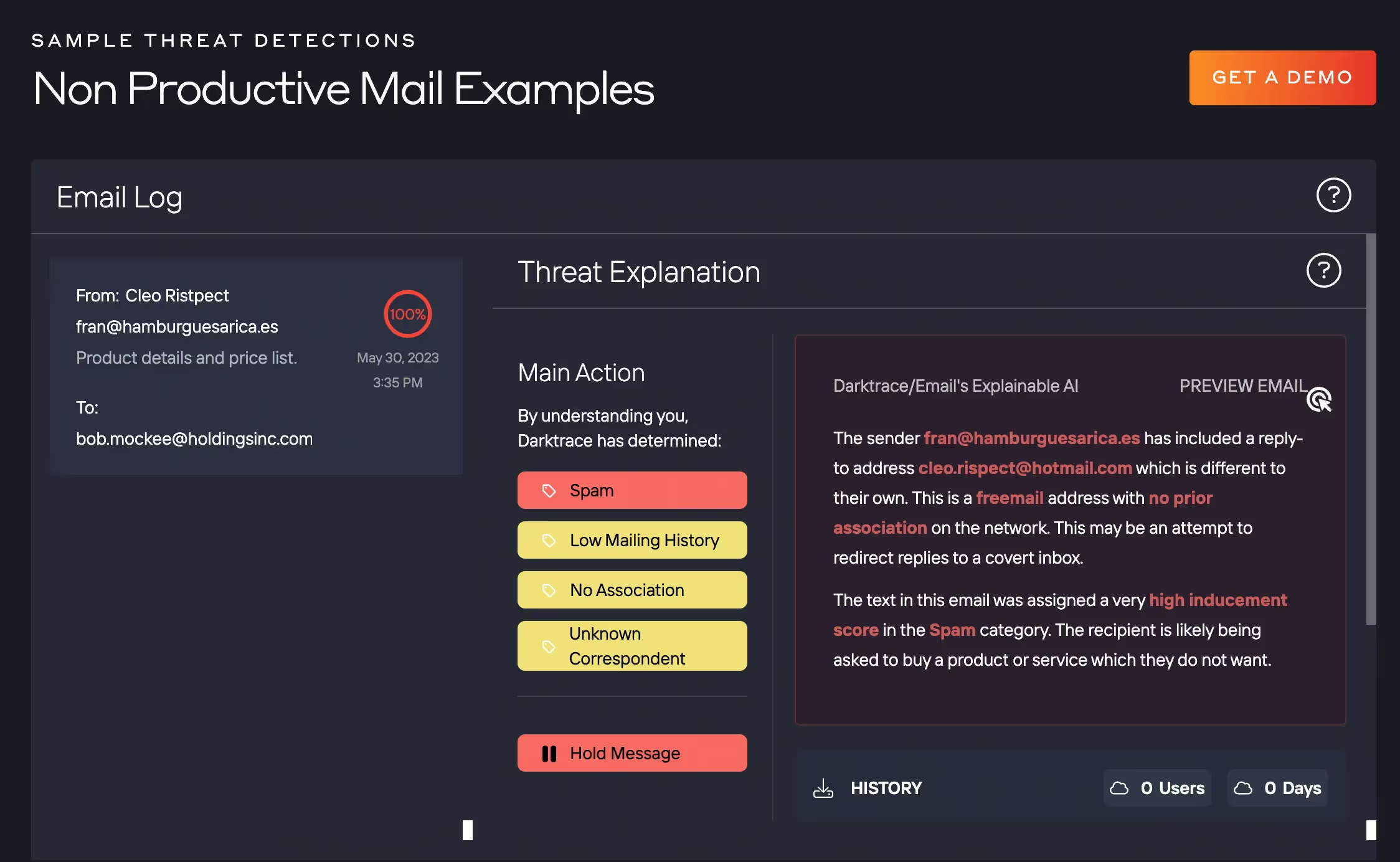
Identifying spam emails can be a time consuming task given that they come in large quantities and from a variety of senders. Automated filtering can maximize productivity of employees and declutter their inboxes while reducing the the workload of the security team. Below is an example of a non-productive email identified in Darktrace/Email's UI. Darktrace/Email can identify and tag emails that are suspicious of spam and other security risks like phishing scams, giving detailed explanation of the potential threat.
How can individuals stop receiving spam?
To reduce the influx of spam emails and protect yourself from the associated risks, there are several effective strategies you can employ. Enhancing your security awareness and taking proactive measures are key to managing spam effectively.
Utilize Spam Filters: Most email services come equipped with built-in spam filters that automatically direct suspicious emails to a spam folder. Adjust these filters to fine-tune their sensitivity, or set up custom filters based on specific criteria to better control what reaches your inbox.
Maintain Email Privacy: It’s essential to keep your email address as private as possible. Avoid sharing it on public forums, social media, or websites where it can easily be harvested by spammers. The less exposure your email has, the harder it is for spammers to find it.
Create Separate Email Accounts: For added security, consider using multiple email addresses. Have one for personal use and another for online transactions or subscriptions. This can limit spam on your primary account and keep essential communications clear of potential spam.
Examine Emails Carefully: Be vigilant about the emails you receive. Spammers often mimic legitimate sources. Check the sender's details by hovering over their name to see if the email address matches the supposed sender, like PayPal. Also, watch for poor spelling or grammar, which are common in spam emails.
Avoid Responding to Spam: Never reply to spam emails. Responding signals to the sender that your email address is active, which can lead to more spam. Instead, mark these emails as marked as spam, which aids your email provider in recognizing and filtering similar future emails.
Exercise Caution with 'Unsubscribe' Links: While unsubscribing seems like a straightforward way to reduce unwanted emails, it can be risky with spam. Spammers might use unsubscribe links to confirm active emails or direct you to malicious sites. It’s safer to mark suspicious emails as spam rather than interacting with them.
Implement Antivirus Protection: Installing robust antivirus software can safeguard your devices if you accidentally interact with a spam message. This software can block malware and potentially harmful websites, providing an additional layer of security for your online activities.
Use Darktrace/Email to Protect Your Email Security: Additionally, consider employing Darktrace/Email for advanced protection. This tool is designed specifically to enhance email security by detecting and isolating threats before they can cause harm.
Challenges organizations face with spam emails
Organizations want to ensure that their employees are able to communicate and conduct business activity without disruption. However, email spam can stand in the way of employees who want to quickly communicate via email. Having an inbox that is cluttered with emails will cause employees to get distracted and have to parse through hundreds of emails just to identity which are legitimate, and which are malicious.
How to protect against spam email
There are several systems in place that protect email inboxes from spam mail. However, some organizations might want to take extensive action in order to protect their employees’ inboxes to ensure business continuity and productivity remain optimal. Email security options include:
Secure email gateways
A secure email gateway (SEG) or a secure email server (SEC) is a type of email security software that sits between inbound and outbound email communication. Every email that is sent to and from an organization passes through this gateway to ensure that its contents are not malicious or a sign of a data leak. It prevents unwanted emails in user inboxes like spam, phishing emails, emails containing malware, etc… In many ways email gateways are the first line of defense for email security.
AI Email solutions
Darktrace / EMAIL uses artificial intelligence and machine learning algorithms to prevent, detect, respond to, and heal from email attacks. Through its unique understanding of you, rather than knowledge of past attacks, Darktrace/Email stops the most sophisticated and evolving email security risks like generative Al attacks, BEC, account takeover, human error, and ransomware.







